# SIEM 이란 무엇인가?
- Security Information and Event Management, 정보 및 이벤트 관리
- SIEM은 IT 네트워크 전반의 데이터를 중앙 집중화하여 보안 문제를 탐지하는 데 사용한다.
- 이는 로그 관리, 보안 이벤트 탐지, 보고 및 검색 기능을 포함한다.
# ELK 란 무엇인가?
- ELK 스택은 Elasticsearch, Logstash, 그리고 Kibana의 세 가지 주요 오픈 소스 프로젝트를 말한다.
Elasticsearch
- 역할: Elasticsearch는 분산형 검색 및 분석 엔진, 대량의 데이터를 신속하게 저장, 검색 및 분석할 수 있다.
- 특징: 고가용성, 확장성, 빠른 검색 성능을 제공, JSON 문서를 기반으로 하며, 복잡한 검색 쿼리를 지원한다.
Logstash
- 역할: Logstash는 서버 사이드 데이터 처리 파이프라인, 다양한 소스에서 데이터를 수집하고 변환한 후 Elasticsearch 에 저장한다.
- 특징: 다양한 입력, 필터, 출력 플러그인을 지원하여 데이터를 수집, 가공 및 보강한다.
Kibana
- 역할: Kibana는 Elasticsearch에 저장된 데이터를 시각화하고 탐색하는 웹 기반 인터페이스
- 특징: 대시보드 생성, 데이터 시각화, 지리적 데이터 매핑, 실시간 데이터 분석 등의 기능을 제공
# 로컬 환경에 Fleet Server(Elastic Agent)를 포함한 ELK 세팅하기 (docker-compose.yml 활용)
프로젝트 GitHub URL : https://github.com/gunh0/whs-utils/blob/ba5798da780b25f34f445530076ed588e901fa47/simple_elk_for_siem/elk-with-fleet/docker-compose.yml

version: "3.8"
volumes:
certs:
driver: local
esdata01:
driver: local
kibanadata:
driver: local
metricbeatdata01:
driver: local
filebeatdata01:
driver: local
logstashdata01:
driver: local
fleetserverdata:
driver: local
networks:
default:
name: elastic
external: false
services:
setup:
image: docker.elastic.co/elasticsearch/elasticsearch:${STACK_VERSION}
volumes:
- certs:/usr/share/elasticsearch/config/certs
user: "0"
command: >
bash -c '
if [ x${ELASTIC_PASSWORD} == x ]; then
echo "Set the ELASTIC_PASSWORD environment variable in the .env file";
exit 1;
elif [ x${KIBANA_PASSWORD} == x ]; then
echo "Set the KIBANA_PASSWORD environment variable in the .env file";
exit 1;
fi;
if [ ! -f config/certs/ca.zip ]; then
echo "Creating CA";
bin/elasticsearch-certutil ca --silent --pem -out config/certs/ca.zip;
unzip config/certs/ca.zip -d config/certs;
fi;
if [ ! -f config/certs/certs.zip ]; then
echo "Creating certs";
echo -ne \
"instances:\n"\
" - name: es01\n"\
" dns:\n"\
" - es01\n"\
" - localhost\n"\
" ip:\n"\
" - 127.0.0.1\n"\
" - name: kibana\n"\
" dns:\n"\
" - kibana\n"\
" - localhost\n"\
" ip:\n"\
" - 127.0.0.1\n"\
" - name: fleet-server\n"\
" dns:\n"\
" - fleet-server\n"\
" - localhost\n"\
" ip:\n"\
" - 127.0.0.1\n"\
> config/certs/instances.yml;
bin/elasticsearch-certutil cert --silent --pem -out config/certs/certs.zip --in config/certs/instances.yml --ca-cert config/certs/ca/ca.crt --ca-key config/certs/ca/ca.key;
unzip config/certs/certs.zip -d config/certs;
fi;
echo "Setting file permissions"
chown -R root:root config/certs;
find . -type d -exec chmod 750 \{\} \;;
find . -type f -exec chmod 640 \{\} \;;
echo "Waiting for Elasticsearch availability";
until curl -s --cacert config/certs/ca/ca.crt https://es01:9200 | grep -q "missing authentication credentials"; do sleep 30; done;
echo "Setting kibana_system password";
until curl -s -X POST --cacert config/certs/ca/ca.crt -u "elastic:${ELASTIC_PASSWORD}" -H "Content-Type: application/json" https://es01:9200/_security/user/kibana_system/_password -d "{\"password\":\"${KIBANA_PASSWORD}\"}" | grep -q "^{}"; do sleep 10; done;
echo "All done!";
'
healthcheck:
test: ["CMD-SHELL", "[ -f config/certs/es01/es01.crt ]"]
interval: 1s
timeout: 5s
retries: 120
es01:
depends_on:
setup:
condition: service_healthy
image: docker.elastic.co/elasticsearch/elasticsearch:${STACK_VERSION}
labels:
co.elastic.logs/module: elasticsearch
volumes:
- certs:/usr/share/elasticsearch/config/certs
- esdata01:/usr/share/elasticsearch/data
ports:
- ${ES_PORT}:9200
environment:
- node.name=es01
- cluster.name=${CLUSTER_NAME}
- discovery.type=single-node
- ELASTIC_PASSWORD=${ELASTIC_PASSWORD}
- bootstrap.memory_lock=true
- xpack.security.enabled=true
- xpack.security.http.ssl.enabled=true
- xpack.security.http.ssl.key=certs/es01/es01.key
- xpack.security.http.ssl.certificate=certs/es01/es01.crt
- xpack.security.http.ssl.certificate_authorities=certs/ca/ca.crt
- xpack.security.transport.ssl.enabled=true
- xpack.security.transport.ssl.key=certs/es01/es01.key
- xpack.security.transport.ssl.certificate=certs/es01/es01.crt
- xpack.security.transport.ssl.certificate_authorities=certs/ca/ca.crt
- xpack.security.transport.ssl.verification_mode=certificate
- xpack.license.self_generated.type=${LICENSE}
mem_limit: ${ES_MEM_LIMIT}
ulimits:
memlock:
soft: -1
hard: -1
healthcheck:
test:
[
"CMD-SHELL",
"curl -s --cacert config/certs/ca/ca.crt https://localhost:9200 | grep -q 'missing authentication credentials'",
]
interval: 10s
timeout: 10s
retries: 120
kibana:
depends_on:
es01:
condition: service_healthy
image: docker.elastic.co/kibana/kibana:${STACK_VERSION}
labels:
co.elastic.logs/module: kibana
volumes:
- certs:/usr/share/kibana/config/certs
- kibanadata:/usr/share/kibana/data
- ./kibana.yml:/usr/share/kibana/config/kibana.yml:ro
ports:
- ${KIBANA_PORT}:5601
environment:
- SERVERNAME=kibana
- ELASTICSEARCH_HOSTS=https://es01:9200
- ELASTICSEARCH_USERNAME=kibana_system
- ELASTICSEARCH_PASSWORD=${KIBANA_PASSWORD}
- ELASTICSEARCH_SSL_CERTIFICATEAUTHORITIES=config/certs/ca/ca.crt
- XPACK_SECURITY_ENCRYPTIONKEY=${ENCRYPTION_KEY}
- XPACK_ENCRYPTEDSAVEDOBJECTS_ENCRYPTIONKEY=${ENCRYPTION_KEY}
- XPACK_REPORTING_ENCRYPTIONKEY=${ENCRYPTION_KEY}
- XPACK_REPORTING_KIBANASERVER_HOSTNAME=localhost
- SERVER_SSL_ENABLED=true
- SERVER_SSL_CERTIFICATE=config/certs/kibana/kibana.crt
- SERVER_SSL_KEY=config/certs/kibana/kibana.key
- SERVER_SSL_CERTIFICATEAUTHORITIES=config/certs/ca/ca.crt
- ELASTIC_APM_SECRET_TOKEN=${ELASTIC_APM_SECRET_TOKEN}
mem_limit: ${KB_MEM_LIMIT}
healthcheck:
test:
[
"CMD-SHELL",
"curl -I -s --cacert config/certs/ca/ca.crt https://localhost:5601 | grep -q 'HTTP/1.1 302 Found'",
]
interval: 10s
timeout: 10s
retries: 120
metricbeat01:
depends_on:
es01:
condition: service_healthy
kibana:
condition: service_healthy
image: docker.elastic.co/beats/metricbeat:${STACK_VERSION}
user: root
volumes:
- certs:/usr/share/metricbeat/certs
- metricbeatdata01:/usr/share/metricbeat/data
- "./metricbeat.yml:/usr/share/metricbeat/metricbeat.yml:ro"
- "/var/run/docker.sock:/var/run/docker.sock:ro"
- "/sys/fs/cgroup:/hostfs/sys/fs/cgroup:ro"
- "/proc:/hostfs/proc:ro"
- "/:/hostfs:ro"
environment:
- ELASTIC_USER=elastic
- ELASTIC_PASSWORD=${ELASTIC_PASSWORD}
- ELASTIC_HOSTS=https://es01:9200
- KIBANA_HOSTS=https://kibana:5601
- LOGSTASH_HOSTS=http://logstash01:9600
- CA_CERT=certs/ca/ca.crt
- ES_CERT=certs/es01/es01.crt
- ES_KEY=certs/es01/es01.key
- KB_CERT=certs/kibana/kibana.crt
- KB_KEY=certs/kibana/kibana.key
command:
-strict.perms=false
filebeat01:
depends_on:
es01:
condition: service_healthy
image: docker.elastic.co/beats/filebeat:${STACK_VERSION}
user: root
volumes:
- certs:/usr/share/filebeat/certs
- filebeatdata01:/usr/share/filebeat/data
- "./filebeat_ingest_data/:/usr/share/filebeat/ingest_data/"
- "./filebeat.yml:/usr/share/filebeat/filebeat.yml:ro"
- "/var/lib/docker/containers:/var/lib/docker/containers:ro"
- "/var/run/docker.sock:/var/run/docker.sock:ro"
environment:
- ELASTIC_USER=elastic
- ELASTIC_PASSWORD=${ELASTIC_PASSWORD}
- ELASTIC_HOSTS=https://es01:9200
- KIBANA_HOSTS=https://kibana:5601
- LOGSTASH_HOSTS=http://logstash01:9600
- CA_CERT=certs/ca/ca.crt
command:
-strict.perms=false
logstash01:
depends_on:
es01:
condition: service_healthy
kibana:
condition: service_healthy
image: docker.elastic.co/logstash/logstash:${STACK_VERSION}
labels:
co.elastic.logs/module: logstash
user: root
volumes:
- certs:/usr/share/logstash/certs
- logstashdata01:/usr/share/logstash/data
- "./logstash_ingest_data/:/usr/share/logstash/ingest_data/"
- "./logstash.conf:/usr/share/logstash/pipeline/logstash.conf:ro"
environment:
- xpack.monitoring.enabled=false
- ELASTIC_USER=elastic
- ELASTIC_PASSWORD=${ELASTIC_PASSWORD}
- ELASTIC_HOSTS=https://es01:9200
fleet-server:
depends_on:
kibana:
condition: service_healthy
es01:
condition: service_healthy
image: docker.elastic.co/beats/elastic-agent:${STACK_VERSION}
volumes:
- certs:/certs
- fleetserverdata:/usr/share/elastic-agent
- "/var/lib/docker/containers:/var/lib/docker/containers:ro"
- "/var/run/docker.sock:/var/run/docker.sock:ro"
- "/sys/fs/cgroup:/hostfs/sys/fs/cgroup:ro"
- "/proc:/hostfs/proc:ro"
- "/:/hostfs:ro"
ports:
- ${FLEET_PORT}:8220
- ${APMSERVER_PORT}:8200
user: root
environment:
- SSL_CERTIFICATE_AUTHORITIES=/certs/ca/ca.crt
- CERTIFICATE_AUTHORITIES=/certs/ca/ca.crt
- FLEET_CA=/certs/ca/ca.crt
- FLEET_ENROLL=1
- FLEET_INSECURE=true
- FLEET_SERVER_ELASTICSEARCH_CA=/certs/ca/ca.crt
- FLEET_SERVER_ELASTICSEARCH_HOST=https://es01:9200
- FLEET_SERVER_ELASTICSEARCH_INSECURE=true
- FLEET_SERVER_ENABLE=1
- FLEET_SERVER_CERT=/certs/fleet-server/fleet-server.crt
- FLEET_SERVER_CERT_KEY=/certs/fleet-server/fleet-server.key
- FLEET_SERVER_INSECURE_HTTP=true
- FLEET_SERVER_POLICY_ID=fleet-server-policy
- FLEET_URL=https://fleet-server:8220
- KIBANA_FLEET_CA=/certs/ca/ca.crt
- KIBANA_FLEET_SETUP=1
- KIBANA_FLEET_USERNAME=elastic
- KIBANA_FLEET_PASSWORD=${ELASTIC_PASSWORD}
- KIBANA_HOST=https://kibana:5601
webapp:
build:
context: app
volumes:
- "/var/lib/docker/containers:/var/lib/docker/containers:ro"
- "/var/run/docker.sock:/var/run/docker.sock:ro"
- "/sys/fs/cgroup:/hostfs/sys/fs/cgroup:ro"
- "/proc:/hostfs/proc:ro"
- "/:/hostfs:ro"
ports:
- 8000:8000
위의 docker-compose.yml 파일을 실행($ docker-compose up)한 뒤,
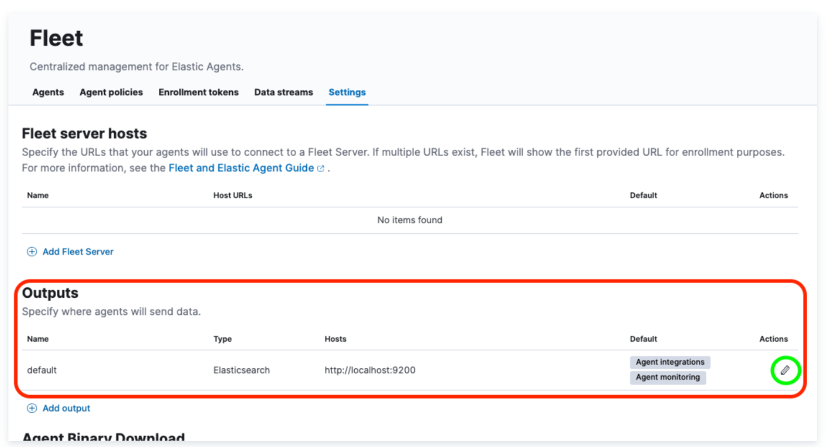
Fleet > Settings 에서 ca.crt 파일을 다음 명령어를 통해 그림과 같이 등록해 준다.
docker cp es-cluster-es01-1:/usr/share/elasticsearch/config/certs/ca/ca.crt ./tmp/.
openssl x509 -fingerprint -sha256 -noout -in ./tmp/ca.crt | awk -F"=" {' print $2 '} | sed s/://g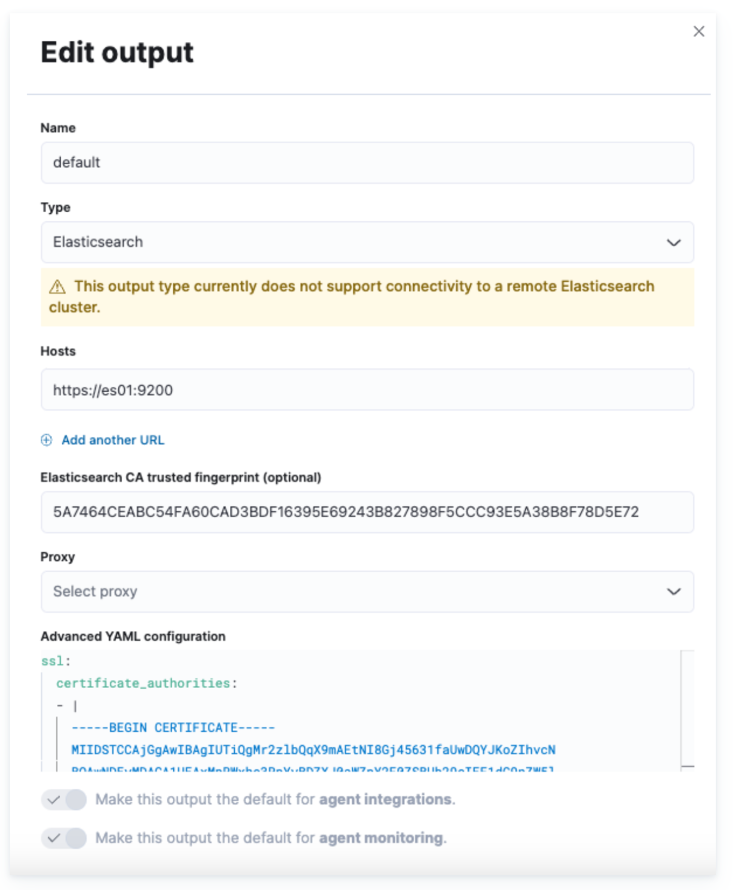
# 정리
위에서 언급한 ELK 스택의 구성 요소들을 효과적으로 활용하기 위해, 로컬 환경에서 Fleet Server(Elastic Agent)를 포함한 ELK 설정을 진행해 보았다. 위에 첨부된 파일(https://github.com/gunh0/whs-utils/tree/ba5798da780b25f34f445530076ed588e901fa47/simple_elk_for_siem/elk-with-fleet)을 통해 ELK 스택을 쉽고 빠르게 구축할 수 있다.
이 docker-compose.yml 파일은 Elasticsearch, Logstash, Kibana, 그리고 Fleet Server를 포함한 ELK 스택의 모든 필수 구성 요소를 포함하고 있어, 보안 정보 및 이벤트 관리(SIEM) 시스템을 효율적으로 구축하고 운영할 수 있는 기반을 제공한다. 이를 통해 로그 관리, 보안 이벤트 탐지 및 분석, 데이터 시각화 등의 작업을 원활하게 수행할 수 있다.
이러한 설정을 통해, 사용자는 보안 관련 데이터를 더욱 효과적으로 관리하고 분석할 수 있으며, 보안 위협에 대응하는 데 필요한 실시간 정보를 얻을 수 있다. 따라서, ELK 스택과 Fleet Server를 활용한 이러한 설정은 보안 전문가들에게 매우 유용한 도구가 될 수 있다.
# Reference
https://www.elastic.co/kr/blog/getting-started-with-the-elastic-stack-and-docker-compose
Getting started with the Elastic Stack and Docker-Compose
In part one of this two-part series, we’ll dive into configuring the components of a standard Elastic Stack consisting of Elasticsearch, Logstash, Kibana, and Beats (ELK-B), on which we can immediatel...
www.elastic.co
https://www.elastic.co/kr/blog/getting-started-with-the-elastic-stack-and-docker-compose-part-2
Getting started with the Elastic Stack and Docker Compose: Part 2
In this blog, build on our previous cluster and implement additional features such as Fleet, Agent, APM, and a demo application for your POC delight! Remember, Docker Compose is not recommended for pr...
www.elastic.co
'Elasticsearch' 카테고리의 다른 글
| [Elasticsearch] 성능 향상을 위한 _id 필드 사용 지양하기 (0) | 2024.02.14 |
|---|
